Current research in the Laboratory of Software Architectures and Information Systems, Lasaris, at the Faculty of Informatics, Masaryk University, is focused on data analysis in the cybersecurity domain.
Subtopics: Visual analytics for cybersecurity training | Behavioral modeling and analysis | Digital forensics
Related projects:
2020 – 2022
Research of New Technologies to Increase the Capabilities of Cybersecurity Experts (KYPOLAB)
My role: Member of the research team, leader of the work package „SW for the evaluation of cybersecurity training“.
2018 – 2023
CyberSecurity, CyberCrime and Critical Information Infrastructures Center of Excellence (C4e)
My role: Member of implementation team (academic staff).
2016 – 2019
Simulation, detection, and mitigation of cyber threats endangering critical infrastructure (KYPO II)
My role: Co-investigator (leader at FI MU, software architect, head of the “visualization” research team).
2013 – 2015
Cybernetic Proving Ground (KYPO)
My role: Co-investigator (leader at FI MU, head of the “visualization” research team).
The project was awarded by the Ministry of Interior for its exceptional results in the field of security research.
Visual analytics for cybersecurity training
Operational networks are not suitable for building and studying knowledge of cyber threats and training responses to them. Therefore, we develop and operate a flexible, scalable, and sophisticated cyber range since 2013, which serves as a virtual environment where hands-on cybersecurity training can be organized.
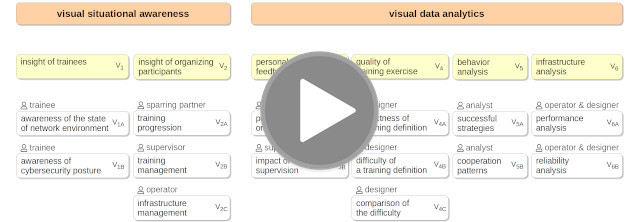
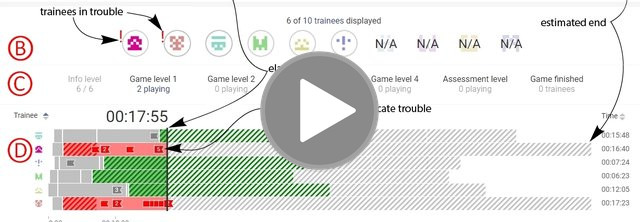
From the very beginning, we put emphasis on user experience, user-centered design of user interfaces, and the support of learning and visual analytics. Data collected from training sessions are analyzed in order to continuously improve the quality of training sessions and increase the impact on the trainees. Our research aims to provide visual situational awareness, insight into the abstract cybersecurity processes and threats, storytelling, and advanced analytical tools.
Software:
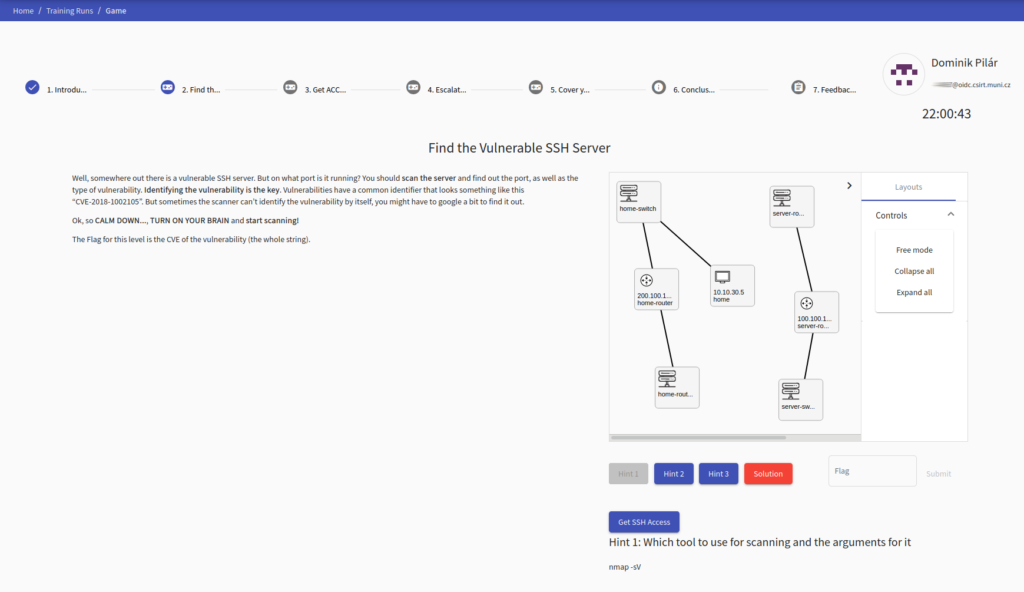
The KYPO Cyber Range Platform is used as a training platform for the regular education of students of Masaryk University as well as for the organization of the biggest cyber defense exercise in the Czech Republic called Cyber Czech (in cooperation with Czech NSA). In 2021 released as open-source.
Awards:
- 2015: Ministry of Interior of the Czech Republic for exceptional security research results.
- 2021: European Commission’s Innovation Radar Prize for Innovation in Disruptive Tech.
Selected publications:
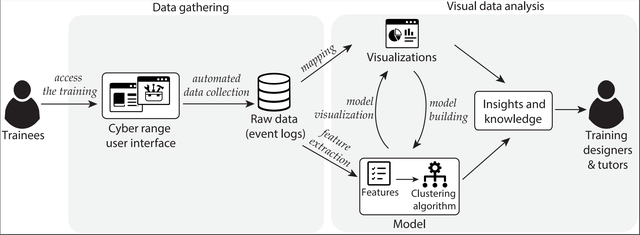
Using data clustering to reveal trainees’ behavior in cybersecurity education
DOČKALOVÁ BURSKÁ, Karolína, Jakub Rudolf MLYNÁRIK and Radek OŠLEJŠEK
Education and Information Technologies (Springer journal, open-access). 2024
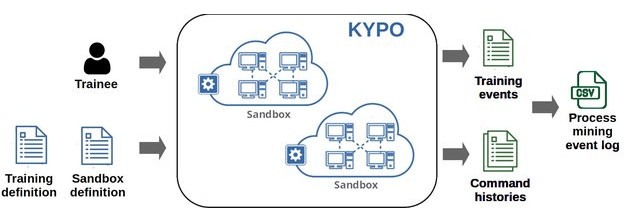
Hands-on Cybersecurity Training Behavior Data for Process Mining
OŠLEJŠEK, Radek, Martin MACÁK and Karolína DOČKALOVÁ BURSKÁ
Data in Brief (Elsevier journal, open-access). 2024
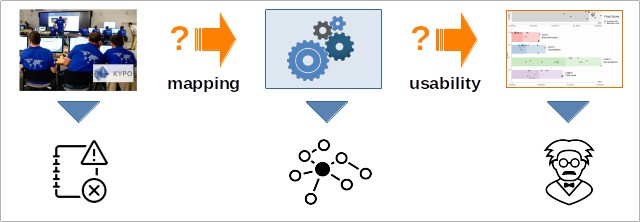
Process Mining Analysis of Puzzle-Based Cybersecurity Training.
MACÁK, Martin, Radek OŠLEJŠEK and Barbora BÜHNOVÁ
ACM Conference on Innovation and Technology in Computer Science Education (ITiCSE’22). 2022
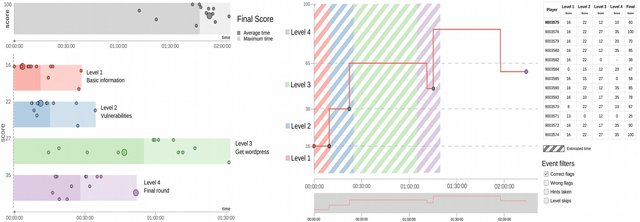
Data-Driven Insight into the Puzzle-Based Cybersecurity Training.
DOČKALOVÁ BURSKÁ, Karolína, Vít RUSŇÁK and Radek OŠLEJŠEK
Computers & Graphics journal. 2022
Conceptual Model of Visual Analytics for Hands-on Cybersecurity Training.
OŠLEJŠEK, R., V. RUSŇÁK, K. BURSKÁ, V. ŠVÁBENSKÝ, J. VYKOPAL and J. ČEGAN
IEEE Transactions on Visualization and Computer Graphics (TVCG journal). 2021
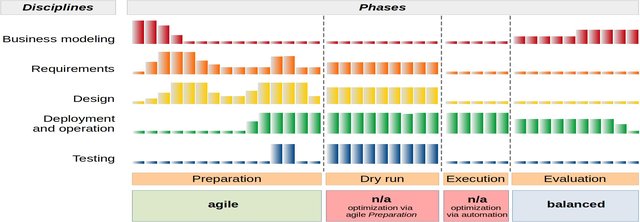
Optimization of Cyber Defense Exercises Using Balanced Software Development Methodology.
OŠLEJŠEK, Radek and Tomáš PITNER
International Journal of Information Technologies and Systems Approach (IJITSA). 2021
Enhancing Situational Awareness for Tutors of Cybersecurity Capture the Flag Games.
DOČKALOVÁ BURSKÁ, Karolína, Vít RUSŇÁK and Radek OŠLEJŠEK
International Conference Information Visualization (iV’21). 2021
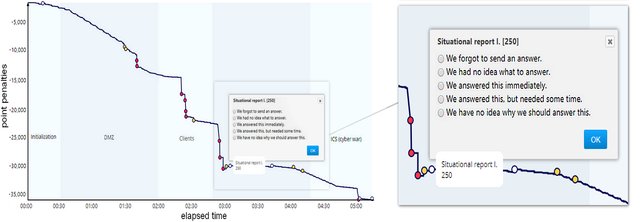
Timely Feedback in Unstructured Cybersecurity Exercises.
VYKOPAL, Jan, Radek OŠLEJŠEK, Karolína BURSKÁ and Kristína ZÁKOPČANOVÁ
ACM Technical Symposium on Computer Science Education (SIGCSE’18). 2018
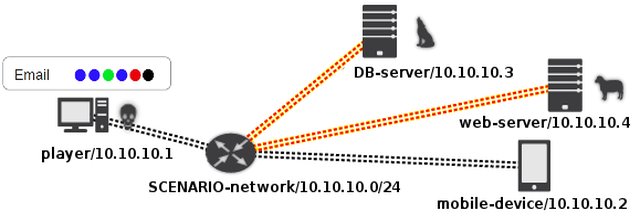
KYPO Cyber Range: Design and Use Cases.
VYKOPAL, Jan, Radek OŠLEJŠEK, Pavel ČELEDA, Martin VIZVÁRY and Daniel TOVARŇÁK
International Conference on Software Technologies (ICSOFT’17). 2017
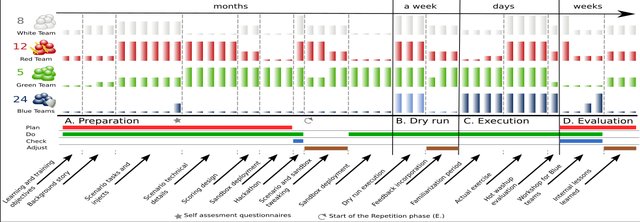
Lessons Learned From Complex Hands-on Defence Exercises in a Cyber Range.
VYKOPAL, Jan, Martin VIZVÁRY, Radek OŠLEJŠEK, Pavel ČELEDA and Daniel TOVARŇÁK
IEEE Frontiers in Education (FIE’17). 2017
Behavioral modeling and analysis
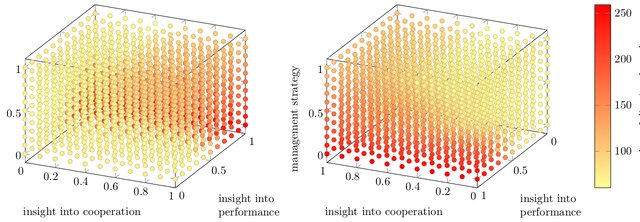
Practical cybersecurity training is strongly process-oriented. There is no tangible output like code to be assessed or compared. Instead, trainees have to solve tasks, e.g, „scan the network and find vulnerable server“ or „exploit the vulnerability to hack the server“. Therefore, process reconstruction and analysis are required to study behavioral patterns or to measure the quality of training sessions. We address these issues in two ways: (a) by designing models and simulations of cooperation strategies on complex networks, and (b) focusing on cybersecurity process discovery, compliance analysis, and behavior analysis for hands-on training programs by means of process mining techniques.
Selected publications:
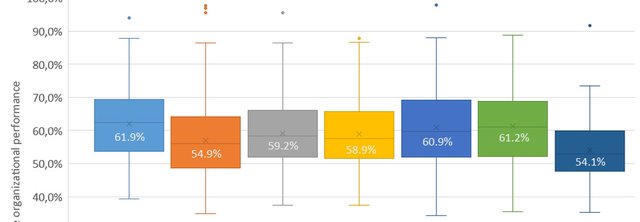
The Prisoner’s Dilemma in the Workplace: How Cooperative Behavior of Managers Influence Organizational Performance and Stress
SPURNÝ, Josef, Ivan KOPEČEK, Radek OŠLEJŠEK, Jaromír PLHÁK and Francesco CAPUTO
Kybernetes. 2021
Simulating the Impact of Cooperation and Management Strategies on Stress and Economic Performance
DAŇA, Josef, Ivan KOPEČEK, Radek OŠLEJŠEK and Jaromír PLHÁK
Hawaii International Conference on System Sciences. (HICSS’19). 2019
Digital forensics
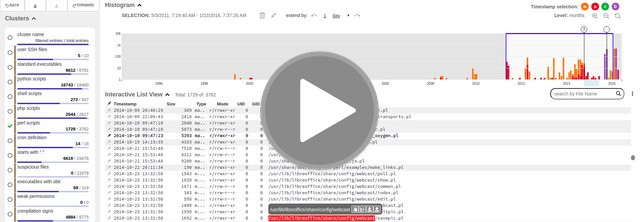
The CSIRT team (Computer Security Incident Response Team) of Masaryk University is responsible for the investigation of suspicious computers connected to the university network. Together with them, we develop advanced visual and exploratory techniques to support the forensic investigation processes. We primarily focus on the analysis of file systems using user-centered design and visual techniques.
Software:
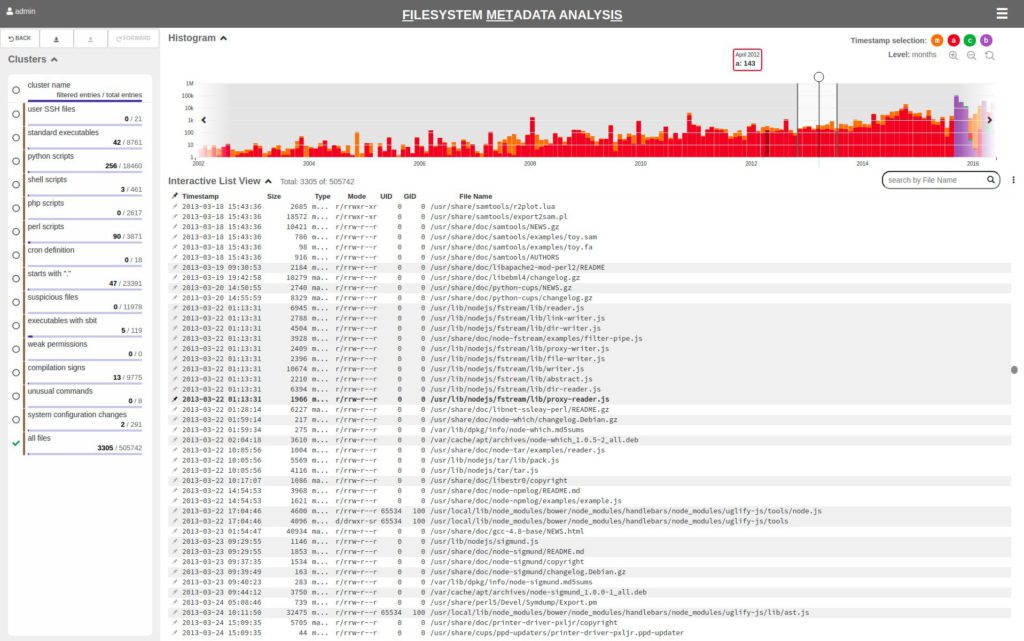
The FIMETIS (FIlesystem METadata analysIS) tool is developed in cooperation with the CSIRT (Computer Security Incident Response Team) team of Masaryk University, which is responsible for the investigation of cybersecurity incidents in the university network. Together with them, we develop advanced visual and exploratory techniques to support the forensic investigation processes. We primarily focus on the analysis of file systems using user-centered design and visual techniques.
Selected publication:
Exploratory Analysis of File System Metadata for Rapid Investigation of Security Incidents
BERAN, Michal, František HRDINA, Dan KOUŘIL, Radek, OŠLEJŠEK, and Kristína ZÁKOPČANOVÁ
IEEE Symposium on Visualization for Cyber Security (VizSec’20). 2020